Latest News
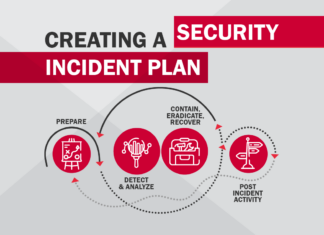
Crafting an Effective Incident Recovery and Remediation Plan: A Strategic Blueprint
In the dynamic realm of cybersecurity, an effective incident recovery and remediation plan stands as the cornerstone for organizational resilience. Beyond mere defense, it ensures a proactive response to potential threats, minimizing...
Alternatives for Let’s Encrypt – Free Automatic CAs
For many, Let's Encrypt has become an integral part of web development, and automatic certificate renewal every 90 days has become a routine. In fact, it is now the most popular certification...
Exploring alternative VPN protocols
The VPN protocol should ideally be secure, functional, and fast. But there is another factor: popularity. An unpopular protocol is more difficult to implement and maintain: its software needs to be installed...
Cryptocurrency-Related Domain Names Hijacked by Phishing GoDaddy’s Registrar Employees
Well-known cybersecurity journalist Brian Krebs reported that employees of the GoDaddy domain registrar were the victims of attacks using social engineering and, as a result, handed over control over the domains of...
What is SOC 2 compliance
About SOC 2
SOC 2 compliance is a crucial framework for technology and cloud computing companies. SOC 2 is a compliance framework for data privacy and security developed...
Directory bruteforce and sensitive files discovery
The brute force (or directory bruteforcing) attack is still one of the most popular password-cracking methods. Nevertheless, it is not just for password cracking.
Brute force attacks can...
Unknowns attack WordPress sites using the Epsilon Framework
Wordfence has discovered a massive attack on WordPress sites. Attackers are actively looking for resources that use themes with the Epsilon Framework, which can be vulnerable to a number of function injection...
Top online courses to improve Python skills
Python is one of the most popular general-purpose high-level programming languages. Due to its fairly simple syntax, flexibility, and scalability, as well as an active global community, it is of great interest...
VBulletin fixed a dangerous vulnerability
VBulletin developers encouraged everyone to update their installations as quickly as possible. The fact is that a critical vulnerability has been fixed in the forum engine. Let me remind you that vBulletin...
How to use torrents safely and legally
Torrents work on P2P technology, when there is no central server or repository, all network participants have the same rights and can download files from dozens (or hundreds) of other computers.