Today we going to emulate quick and simple vulnerability assessment of our web application with help of some open source security tools. List of tools we going to use is available below:
- Google & Shodan – recon (passive)
- BlackWidow – recon (active)
- Sqlmap – sql injections detection
- nmap – server security assessment
- BruteX – brute force attacks
- XSScrapy – cross-site scripting detection / fuzzing
- Dirb – directory enumeration
For short penetration test I think this toolkit should be enough. Ok, so let’s move and start doing our first steps. At the beginning we need to gather some information with which we going to work on other steps.
First of all I recommend to use such sources of information like Google and Shodan. For google interesting and useful dorks we can find with help of exploit-db or other sources.
Recon
Searching in Google with following query: “site:AU intext:sql syntax error”
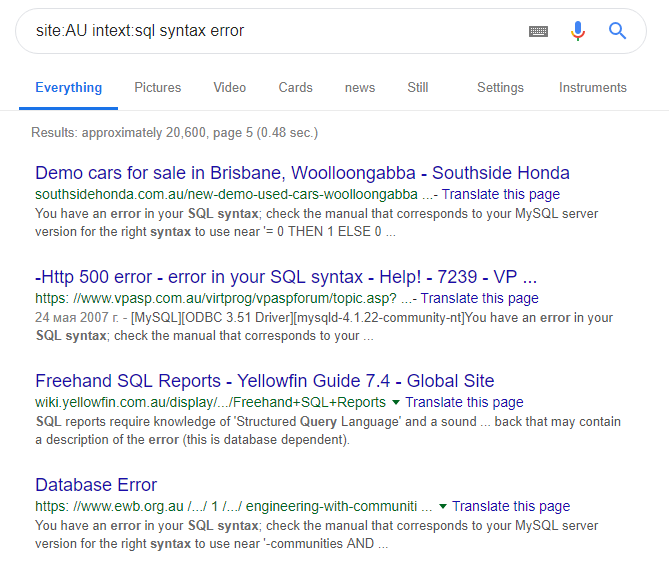
And so here we got several potential targets which we can in future check with sqlmap or by using manual sql injection techniques. Here I think we have done, as I’m not going to execute any other actions against vulnerable systems. However from my experience there high percentage that some of this hosts are vulnerable and it is possible to get data from DB in worst case and in best case – even take over the whole server (example of server takeover through sqli).
Let’s do some research again, but now going to check our own website:
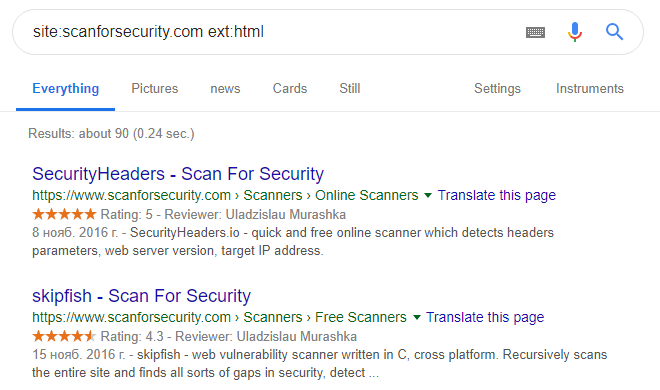
Good, we can see all available files with html extension within our domain name. This way we can try to find out for example directories with files listing possibility, outdated or backed up php files, database backup files and much more.
Additionally we now going to check our website with blackwidow tool to grab dynamic urls, find some additional helpful data including possible subdomains:
$ blackwidow -u https://www.scanforsecurity.com
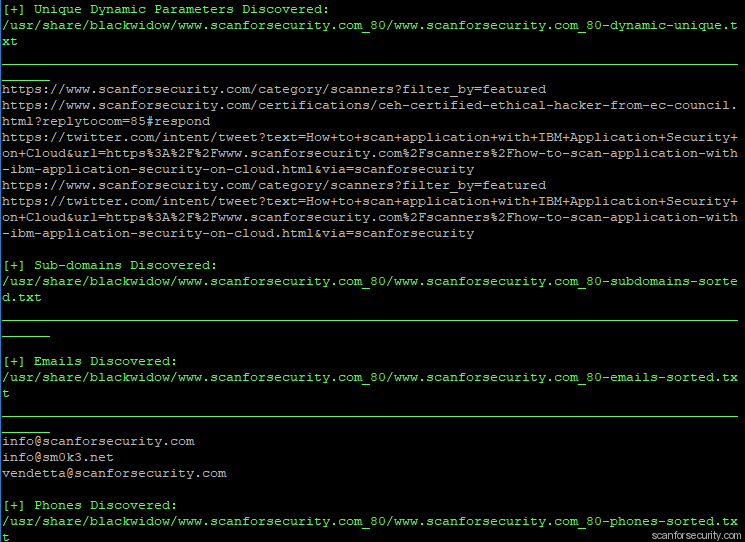
On the screenshot above we see that it has found us several dynamic urls which we can send to sqlmap for additional check and emails which we can use for potential fishing attacks.
Scanning & Vulnerabilities identification
Let’s try to send 1 uri to sqlmap:
$ sqlmap -u https://www.scanforsecurity.com/category/scanners?filter_by=featured --threads=3 --level=4 --risk=2 --dbms=mysql --random-agent --dbs --batch
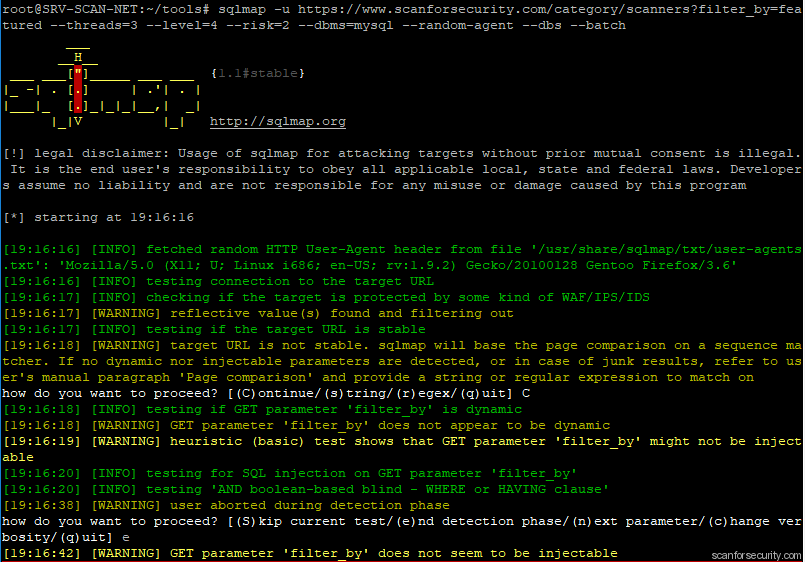
We did test our url and can see that it is actually not vulnerable. In such case we can somehow change sqlmap configuration and try to go harder or even switch and try exploit potential vulnerability with manual approach.
Next step will be scanning with nmap for available services and possible vulnerabilities:
$ nmap -sV -T4 scanforsecurity.com -F --script vuln
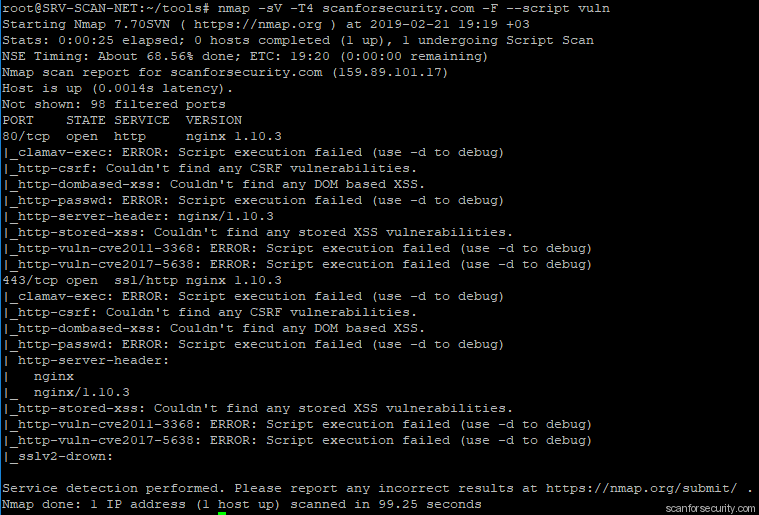
In case if on our server were running some services which requires authentication, like: ftp, samba, ssh, rdp, database or anything else – we could use BruteX tool. It is very simple to use, you just need to enter the target:
$ brutex scanforsecurity.com
This tool actually consist of nmap, hydra, dnsenum and something similar. By default it will scan your server for specific open ports and than try to brute force them with it default user/pass list. It uses preconfigured quick nmap scan and hydra scan. In case if something will be found – you will be alerted.
Last 2 steps are actually a bit less interesting but still applicable. Just for your information – sqlmap can find XSS vulnerabilities as well, some kind of header injections will be executed (just check again screenshot above) with help of nmap. But still we can try to fuzz our application with xsscrapy:
$ ./xsscrapy.py -u https://www.scanforsecurity.com/
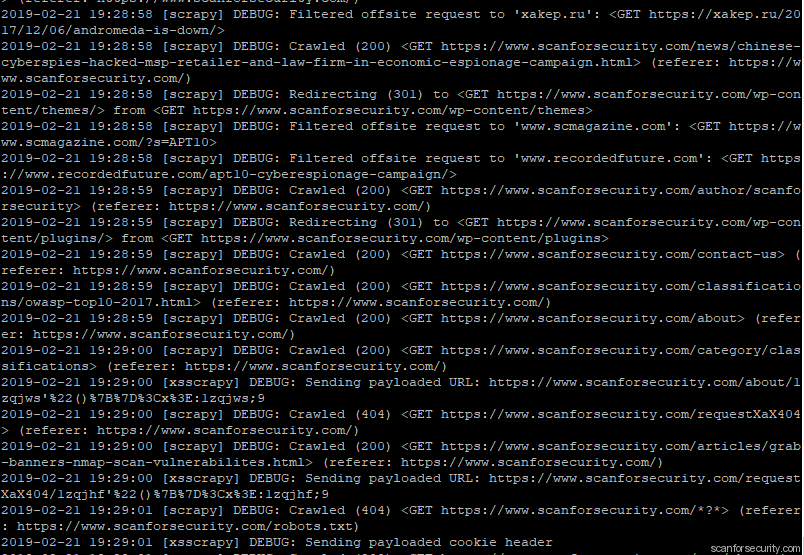
Of course xsscrapy didn’t find anything, but as it shown on the screenshot – during the process of fuzzing it generates loads of test requests which must help identify possibility of XSS and with lower percentage – sqli vulnerabilities.
Optionally during our assessment we may try to execute dirb. If you have found SQL Injection and want to try upload your shell, it will be helpful to get information about available folders and website structure. Sometimes dirb may help you with finding of sensitive files and folders. It can be used during recon process or as additional tool during exploitation of sql injection and file uploading process.
$ dirb https://www.scanforsecurity.com
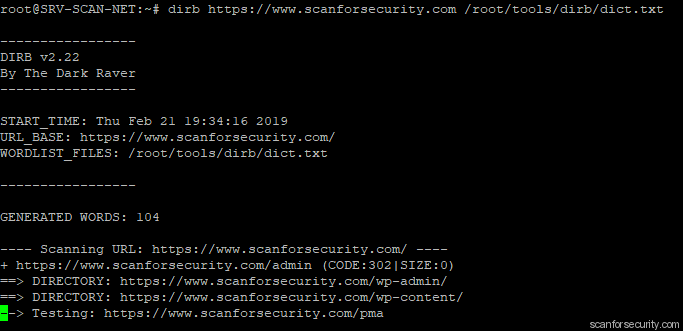
Dirb have found potential admin panel and also such directories like “wp-…” which means that we working with website based on WordPress.
Hint: Identify type of CMS, web server and some more information you may obtain by using web browser plugin “Wappalyzer”, it analyzes target website and provides you with information on the fly.
Afterwords
Please, pay attention that we didn’t execute full scale black box penetration testing. Here we just did some simple vulnerability assessment with basic OSINT/Recon and tried to scan and identify some popular kind of vulnerabilities.
If you mentioned, there no need to huge amount of tools for such activities, you’ll need just proper approach, some knowledge’s and basic understanding of how things works.
Don’t try to execute any kind of attacks against web applications or server you don’t own as this is illegal.