A joint group of researchers from the Worcester Polytechnic Institute (USA), the University of Lubeck (Germany) and the University of California at San Diego (USA) revealed details of two problems, collectively called TPM-FAIL. The bugs are associated with the Trusted Platform Module (TPM) and allow you to retrieve the cryptographic keys stored in the TPM.
The danger of TPM-FAIL is due to the fact that, according to researchers, such attacks can be successfully used in real life, which is rare for TPM attacks in general. Since today it is difficult to find a device that does not use TPM in the form of a hardware-isolated chip or software solution, billions of devices are potentially vulnerable to the problem, from PCs, laptops and servers to IoT.
TPM-FAIL consists of two vulnerabilities:
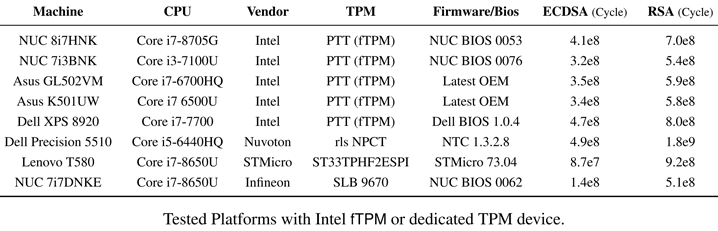
- The first issue is CVE-2019-11090, which is related to Intel Platform Trust (PTT) technology. Intel PTT is a TPM software solution for Intel fTPM that is widely used on servers, desktops, and laptops. It is supported by all Intel processors released since 2013, that is, starting with the Haswell generation;
- The second problem is CVE-2019-16863, associated with ST33 TPM chips manufactured by STMicroelectronics. ST33 TPM is very popular and is used in a wide variety of devices, from network equipment to cloud servers. This is one of the few chips that have received the CommonCriteria (CC) EAL 4+ classification, that is, it comes with built-in protection against side-channel attacks.
It is worth saying that specialists studied other TPM solutions, including those from Infineon and Nuvoton, but they were recognized as reliable.
In essence, TPM-FAIL attacks are a timing leakage problem, that is, a potential attacker can observe how the TPM performs repetitive operations and observe the time difference. By analyzing this data and based on how much time the TPM spends on the same operations, the attacker is able to extract information processed inside the TPM.
According to researchers, the attack can be used to extract 256-bit private keys stored in TPM. Such 256-bit keys are used by certain digital signature schemes based on elliptic curve algorithms, for example, ECDSA and ECSchnorr. As a result, cryptographically protected operations such as establishing TLS connections, signing digital certificates, and authorizing logins are at risk.
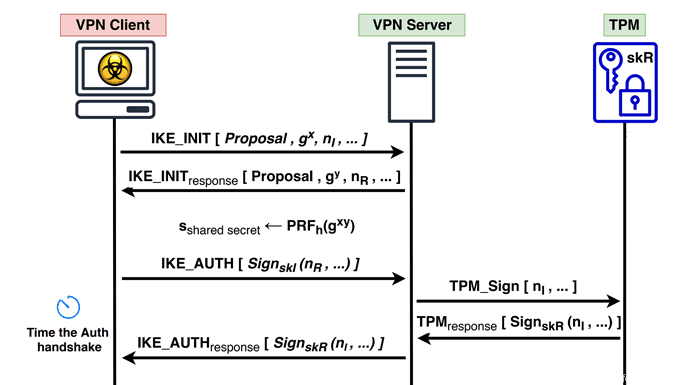
It is emphasized separately that TPM-FAIL attacks do not take too much time. So, recovering an ECDSA key from Intel fTPM is possible in 4-20 minutes, depending on the access level. Researchers claim that attacks can also be carried out remotely in fast networks, for example, it took about 5 hours for specialists to recover the VPN server authentication key and required about 45,000 authentication handshakes and a careful study of server responses.
Intel representatives have already published official security recommendations and released updates for Intel PTT. STMicroelectronics developers, in turn, could not just release a software update and instead prepared a new version of the ST33 chip, which, as the researchers have already confirmed, is resistant to TPM-FAIL attacks.
In the future, a team of researchers plans to publish on GitHub the tools they used to analyze vulnerable TPMs, as well as PoC exploits.

























