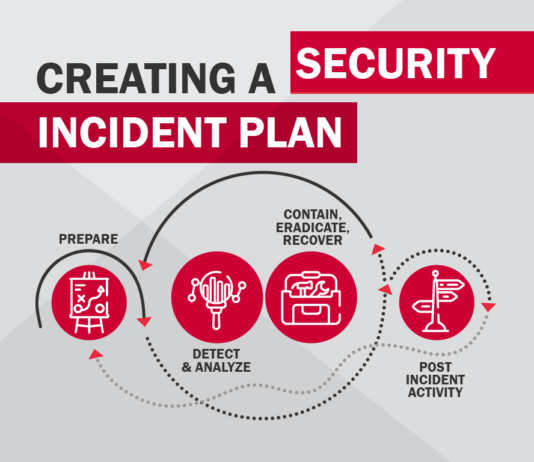
Directory bruteforce and sensitive files discovery
The brute force (or directory bruteforcing) attack is still one of the most popular password-cracking methods. Nevertheless, it is not just for password cracking.
Brute...
Top online courses to improve Python skills
Python is one of the most popular general-purpose high-level programming languages. Due to its fairly simple syntax, flexibility, and scalability, as well as an active global community, it is...
How to use torrents safely and legally
Torrents work on P2P technology, when there is no central server or repository, all network participants have the same rights and can download files from dozens (or hundreds) of...
15 tips to protect against spying on your smartphone
Mobile phones have long become an integral part of our personal space. However, with the growing number of cyber crimes and the popularity of third-party applications, the confidentiality of...
Weapons of mass delusion: 10 simple recipes for successful social engineering
What is social
engineering?
Social engineering, in the context of information security, is the psychological manipulation of people into performing actions or divulging confidential information. This...
Penetration Testing for GDPR
What is GDPR?
The General Data Protection Regulation (GDPR) is focused on the personal data of citizens within the European Union. GDPR is often viewed...
TPM-FAIL Vulnerabilities Threaten PCs, Laptops, Servers, and Other Devices
A joint group of researchers from the Worcester Polytechnic Institute (USA), the University of Lubeck (Germany) and the University of California at San Diego (USA) revealed details of two...
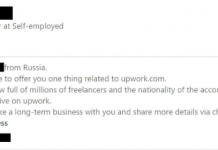
Someone asked to share UpWork account
Over the past couple of years, there have been more frequent cases with requests to provide access to the account on UpWork for money. Usually people ask to provide...
Useful tools for OSINT
What is OSINT?
Open Source Intelligence, or "OSINT," was defined by the Department of Defense (DoD) as “produced from publicly available information that is collected,...
2019’s Most Common IoT Security Threats to Consider
Being used
in hitherto unheard of sectors, IoT is gaining momentum day in day out! Due to
which more and more companies are jumping on the IoT bandwagon with various
point solutions...