Fresh news came about phishers from Iran. Actually for last year if trust many information sources regarding hacking activities from Iran have grown a lot and nobody knows which events it tied to but possibly some kind of political games as well.
The group of Iranian hackers the US charged last week with hacking over 300 universities across the globe were actually master phishers astute at their craft, so much so that they used the same phishing lure for years without needing to change it.
This information was not included in the official indictment released last week but published yesterday in a report by PhishLabs, a company that detected and tracked the group, and later shared some of its findings with investigators.
Hackers used the same “library” angle for 4 years
PhishLabs says the Iranian group —known as the Mabna hackers— used the same phishing lure for four years, since at least February 2014.
Besides small spelling error corrections, the message remained the same until late last year, when PhishLabs stumbled over the group’s existence.
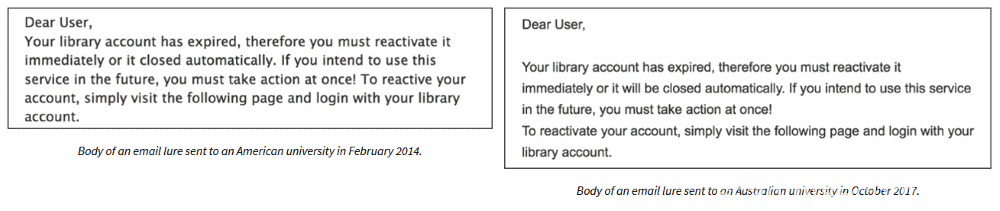
In most email operations PhishLabs managed to discover and later trace back to the group (which they tracked as Silent Librarian), the spear-phishing email was a message that appeared to come from the university’s network, asking users to reactivate their library account.
Silent Librarian phishing lure
“Overall, the lures constructed by Silent Librarian are remarkably authentic-looking,” said Crane Hassold, Director of Threat Intelligence at PhishLabs. “Spelling and grammar, two of the primary indicators of a malicious email, are nearly perfect. The message in the lures are contextually legitimate, meaning it is an email a recipient could be reasonably expected to receive.”
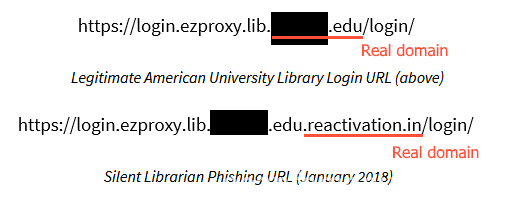
All emails came from spoofed email addresses, made to look like they were coming from inside the network, but including links to domains that tried to mirror the real library URL as much as possible.
Links used in the phishing emails
Furthermore, the emails were highly customized and unique for each targeted university, down to the librarian’s names, and the email signature.
Phishing lures barely changed because they were so successful
“Silent Librarian phishing campaigns [and] tactics have barely changed over time,” Hassold says. “Outside the correction of a few minor spelling errors, the content of the phishing lures has remained incredibly consistent.”
“The likely reason for this consistency is that the success rate of campaigns using these lures was high enough that there was no need for them to evolve,” he added.
It’s because of this level of attention to details that the attacks were so successful. The FBI said hackers breached 144 US universities and 176 universities in 21 foreign countries, from where they stole over 31.5 terabytes of academic data and intellectual property.
Hackers targeted more than 100,000 professors, successfully compromising 8,000 accounts. But Hassold says the group also targeted students and not only professors.
PhishLabs uncovers third-site used for selling accounts
The hackers were interested in collecting login credentials for these accounts, which they later used to extract academic research and intellectual properties stored in these private university networks.
The Mabna (Silent Librarian) hackers passed this info to Iran’s Islamic Revolutionary Guard Corps (IRGC), but they also sold it online on two websites —Megapaper.ir (Megapaper) and Gigapaper.ir (Gigapaper), portals operated by a company controlled by one of the nine suspects. They also used the same sites to sell access to compromised university accounts.
Hassold says he also discovered a third website (Uniaccount.ir), which the FBI appears to have missed, and which according to domain data, was also operated by one of the nine hackers charged last week.
In addition, ClearSky Security also discovered three other similar websites as well.
All in all, we rarely see a phishing campaign that was so successful and well put together as the one conducted by the Mabna (Silent Librarian) crew. But, in hindsight, by not changing the phishing lure, hackers also left a trail of their entire operation behind, which the PhishLabs crew was easily able to track down and pass on to authorities.
So be careful with emails and don’t trust unknown senders. If you received email from an unknown person better move it to trash and don’t open any attachments.
























thanks for quick information security news updates!
Comments are closed.