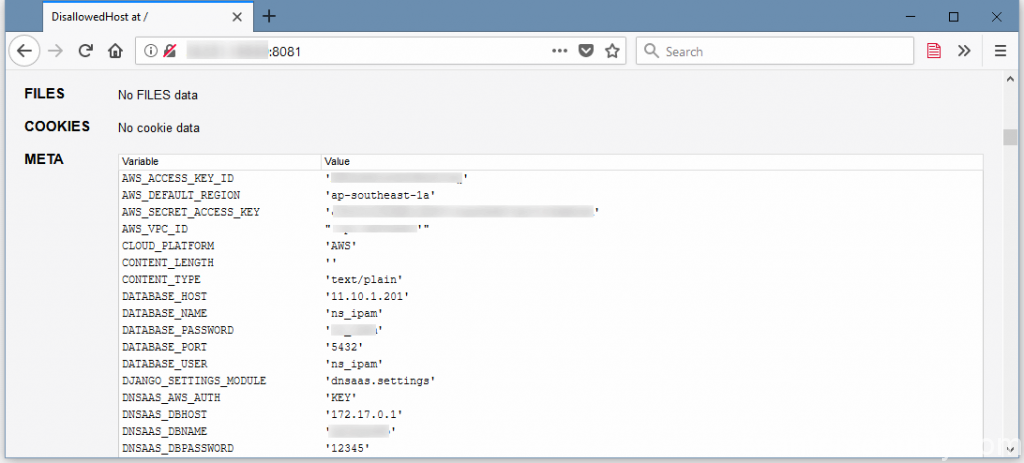
Security researchers have begun stumbling upon misconfigured Django applications that are exposing sensitive information such as API keys, server passwords, or AWS access tokens.
The main reason for this exposure is because app developers forget to disable a Django app’s debug mode, Brazilian security researcher Fábio Castro told Bleeping Computer earlier this week.
Django, which is a very powerful and customizable Python framework, is often used in creating Python-based web applications, intranets, and app backends.
28,165 leaky Django apps found on Shodan
Castro told Bleeping Computer that he discovered this week 28,165 Django apps for which admins forgot debug mode enabled.
Just by skimming through a few of the servers, the researcher found that the debug mode of many of these apps were exposing extremely sensitive information that would have allowed a malicious actor full access to the app owner’s data. The more complex the Django app, the higher the change to find more sensitive information.
Database passwords and AWS access tokens could in some cases also allow access to more than an app’s data, and an attacker could also access information from other parts of the app owner’s IT infrastructure.
Not a failure on Django’s side
“I found this as I was working with the Django framework on a small project,” Castro told Bleeping Computer in a private conversation. “I noticed some error exception and then went searching on Shodan.”
“The main reason [for all the exposures] is the debug mode enabled,” Castro says. “This is not a failure from Django’s side. My recommendation is to disable debugging mode when deploying the application to production.”
Castro is, indeed, right. After more than 25 years of web development, you’d think developers would have learned by now never to leave debug mode enabled for their sites and web apps, regardless of their development stack.
Speaking to Bleeping Computer, Gevers says he found at least one compromised server, running the Weevely web shell. Some servers Gevers found leaking sensitive data belonged to various government agencies carrying out critical operations.
Gevers said he started notifying servers owners about their leaky Django apps. “At this moment we have reported 1,822 servers,” Gevers said. “143 were fixed or taken offline.”