OWASP Top 10 list was updated and currently there is OWASP TOP10 2017 RC is available.
Big variety of standards, tools, and organizations, including Mitre, PCI DSS, DISA, FTC, and many others refers on OWASP TOP 10 project.
Owasp Top 10 is a recognized methodology for assessing the vulnerability of Web applications around the world.
The version of the standard is updated approximately every three years and reflects current trends in Web application security.
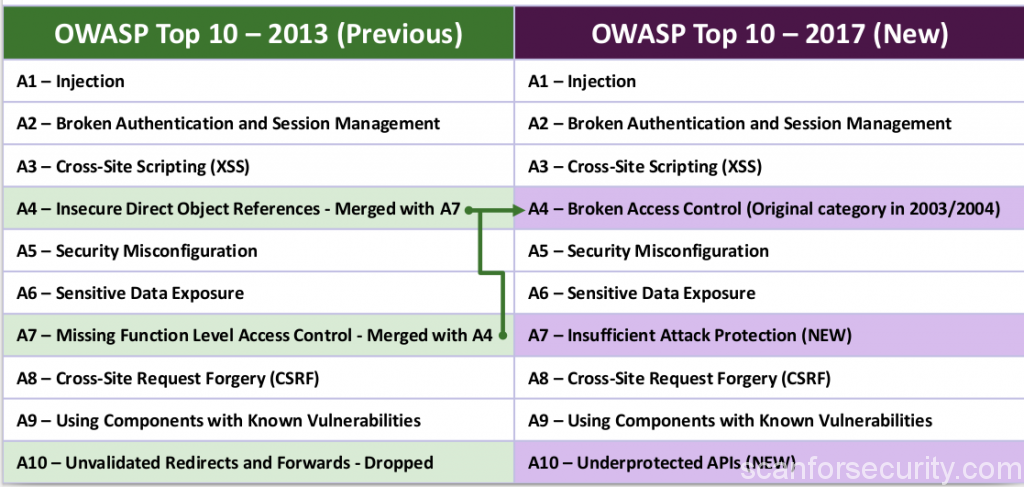
OWASP TOP10 list from 2013:
- A1 Injection
- A2 Broken Authentication and Session Management (was formerly 2010-A3)
- A3 Cross-Site Scripting (XSS) (was formerly 2010-A2)
- A4 Insecure Direct Object References
- A5 Security Misconfiguration (was formerly 2010-A6)
- A6 Sensitive Data Exposure (2010-A7 Insecure Cryptographic Storage and 2010-A9 Insufficient Transport Layer Protection were merged to form 2013-A6)
- A7 Missing Function Level Access Control (renamed/broadened from 2010-A8 Failure to Restrict URL Access)
- A8 Cross-Site Request Forgery (CSRF) (was formerly 2010-A5)
- A9 Using Components with Known Vulnerabilities (new but was part of 2010-A6 – Security Misconfiguration)
- A10 Unvalidated Redirects and Forwards
Updated OWASP TOP10 2017 RC list:
- A1 Injection
- A2 Broken Authentication and Session Management
- A3 Cross-Site Scripting (XSS)
- A4 Broken Access Control (As it was in 2004)
- A5 Security Misconfiguration
- A6 Sensitive Data Exposure
- A7 Insufficient Attack Protection (NEW)
- A8 Cross-Site Request Forgery (CSRF)
- A9 Using Components with Known Vulnerabilities
- A10 Underprotected APIs (NEW)
As you can see, some vulerability types positions were changed, some types disappeared and two new types appeared in the list (marked as NEW).
Changes
The first three types are: injection of code, session management and storage deficiencies and the Cross-site scripting remain unchanged, indicating that despite the large number of best practices in writing secure code, data cleanup, embedding a variety of tokens, and other things, web applications do not become safer.
In 4th place, the old category returned is broken access control, which, in the new revision, consists of the A7 from the 2013 edition.
The 7th place now occupies a new category, Insufficient Attack Protection.
Up to date document in PDF you can find here.